
Capability: Expertise
Our interdisciplinary teams have one goal: to limit the consequences of adverse events by minimizing vulnerabilities to protect your people and your critical assets.

 © Richard Bryant/Arcaidimages.com
© Richard Bryant/Arcaidimages.com
Whether you’re an architect, owner, developer, educational institution or public agency, we help you achieve your security objectives. We partner with project stakeholders to fully understand the unique requirements of your project – whatever its type, size or location, new or existing – then craft solutions that provide the right level of protection. That integrate seamlessly into your design and operational plans. And fit your budget.
We assess vulnerability to multiple hazards and provide balanced strategies to maximize physical, operational and electronic security. We start by making sure our clients know about all the available options, then we work together to set appropriate performance targets and levels of protection. Only then do we start to select the combination of design solutions best suited to each project.
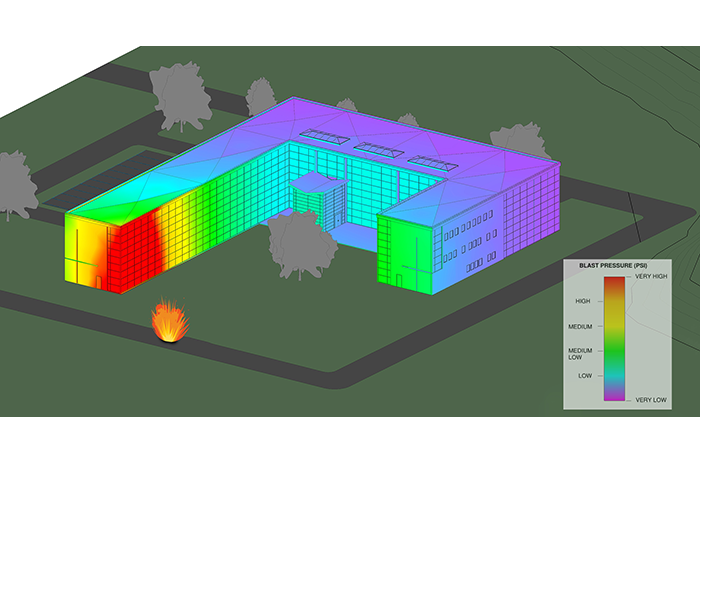
While the threat of terrorist attacks against buildings has increased, recent innovations have greatly improved protective design and security strategies. We use the best-available tools to accurately predict how building materials react to high-explosive waves. We mine data and analyze threat risks. And when commercially available tools don’t do the job well enough, we work with our R&D and technology specialists to develop new applications.
We have unparalleled experience in protective design and security services for U.S. and U.K. government agencies like the U.S. Department of Defense (DOD), U.S. General Services Administration (GSA), U.S. Department of State Bureau of Overseas Building Operations (including U.S. embassies), and U.K. Ministry of Defence (MOD).
We’re also experienced in providing protective design and security services for facilities across a spectrum of market sectors, including: aviation, commercial and residential, critical facilities, education, energy, healthcare and research, sports and public assembly, tall and supertall buildings, and transportation.

Martyn’s Law 2025: U.K. Venue Security & Compliance for the Built Environment
Risk Mitigation for Workplace Design
Pittsburgh Int'l Airport Featured in Modern Steel Construction
What England's Building Safety Act Means for Forensic Engineers and Insurers
Bob Smilowitz Recognized With ASCE Award